New Delhi: As the Internet faces one of the most serious vulnerabilities in recent years putting millions of devices at hacking risk, attackers are now making thousands of attempts to exploit a second vulnerability involving a Java logging system called 'Apache log4j2'.
The description of the new vulnerability, titled 'CVE 2021-45046', says the fix to address the earlier security bug (CVE-2021-44228) in 'Apache Log4j 2.15.0' was "incomplete in certain non-default configurations".
"It was found that the fix to address CVE-2021-44228 in Apache Log4j 2.15.0 was incomplete in certain non-default configurations.
"This could allow attackers... to craft malicious input data using a JNDI Lookup pattern resulting in a denial of service (DOS) attack," the CVE description read.
Several popular services, including Apple iCloud, Amazon, Twitter, Cloudflare and Minecraft, are vulnerable to the 'ubiquitous' zero-day exploit.
Apache has now released a new security patch to address the second bug.
'Apache Log4j' is used in many forms of enterprise and open-source software, including cloud platforms, web applications and email services.
It is the most popular java logging library with over 400,000 downloads from its GitHub project. It is used by a vast number of companies worldwide, enabling logging in a wide set of popular applications.
"Exploiting this vulnerability is simple and allows threat actors to control java-based web servers and launch remote code execution attacks," cyber security researchers at Check Point had said in a blog post.
Another cyber security company Sophos said that it is already detecting malicious cryptominer operations attempting to leverage the vulnerability, and there are credible reports from other sources that several automated botnets (such as Mirai, Tsunami, and Kinsing) have begun to exploit it as well.
At present, most of the attacks focus on the use of cryptocurrency mining at the expense of the victims. However, under the auspices of the noise, more advanced attackers may act aggressively against quality targets.
Researchers at Microsoft have also warned about attacks attempting to take advantage of 'Log4j' vulnerabilities, including a range of crypto-mining malware.
Internet faces greater risk as 2nd serious bug found, patch released
The description of the new vulnerability, titled 'CVE 2021-45046', says the fix to address the earlier security bug (CVE-2021-44228) in 'Apache Log4j 2.15.0' was "incomplete in certain non-default configurations".
IANSUpdated: Thursday, December 16, 2021, 09:06 AM IST

RECENT STORIES
FPJ Exclusive: Realme 15T Review – Is This The Best Budget iPhone-Style Smartphone In India?

Realme 15T With iPhone-Like Design, 7,000mAh Battery Launching In India Today: How To Watch Live

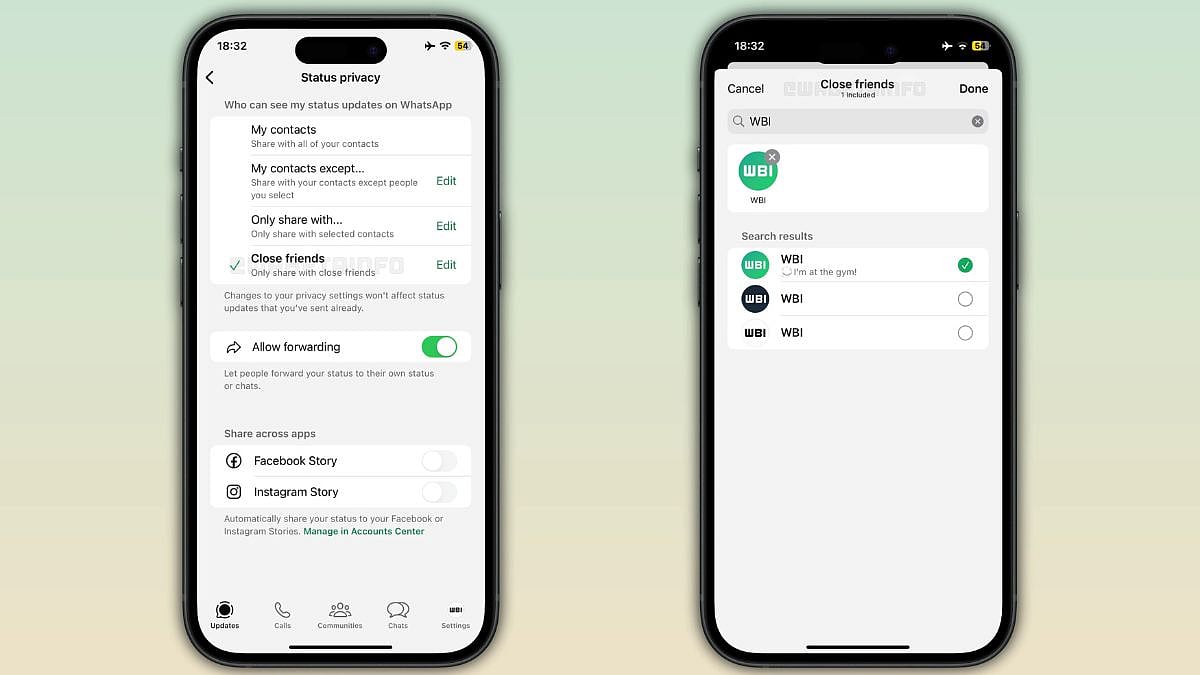
WhatsApp To Bring New 'Close Friends' List Feature Just Like Instagram
iOS 26 Rollout Expected Mid-September Following Apple's iPhone 17 Launch Event: Compatible Devices,...

Salesforce Lays Off 4,000 Employees As AI Handles Half Of Customer Service Tasks


