After website defacement and data leaks, DragonForce Malaysia, the hacker group behind the ongoing cyber attack against India, has now moved on to ransomware attacks.
DragonForce had on June 10 issued a call to all hackers, asking them to join the campaign dubbed OpsPatuk, meant to be revenge against suspended BJP spokesperson Nupur Sharma’s derogatory comments about the Prophet Mohammed. The first wave of OpsPatuk included hacking and defacement of hundreds of Indian websites, both government and private, while in the second waves, DragonForce hacked servers of organisations and leaked personal data of lakhs of Indians.
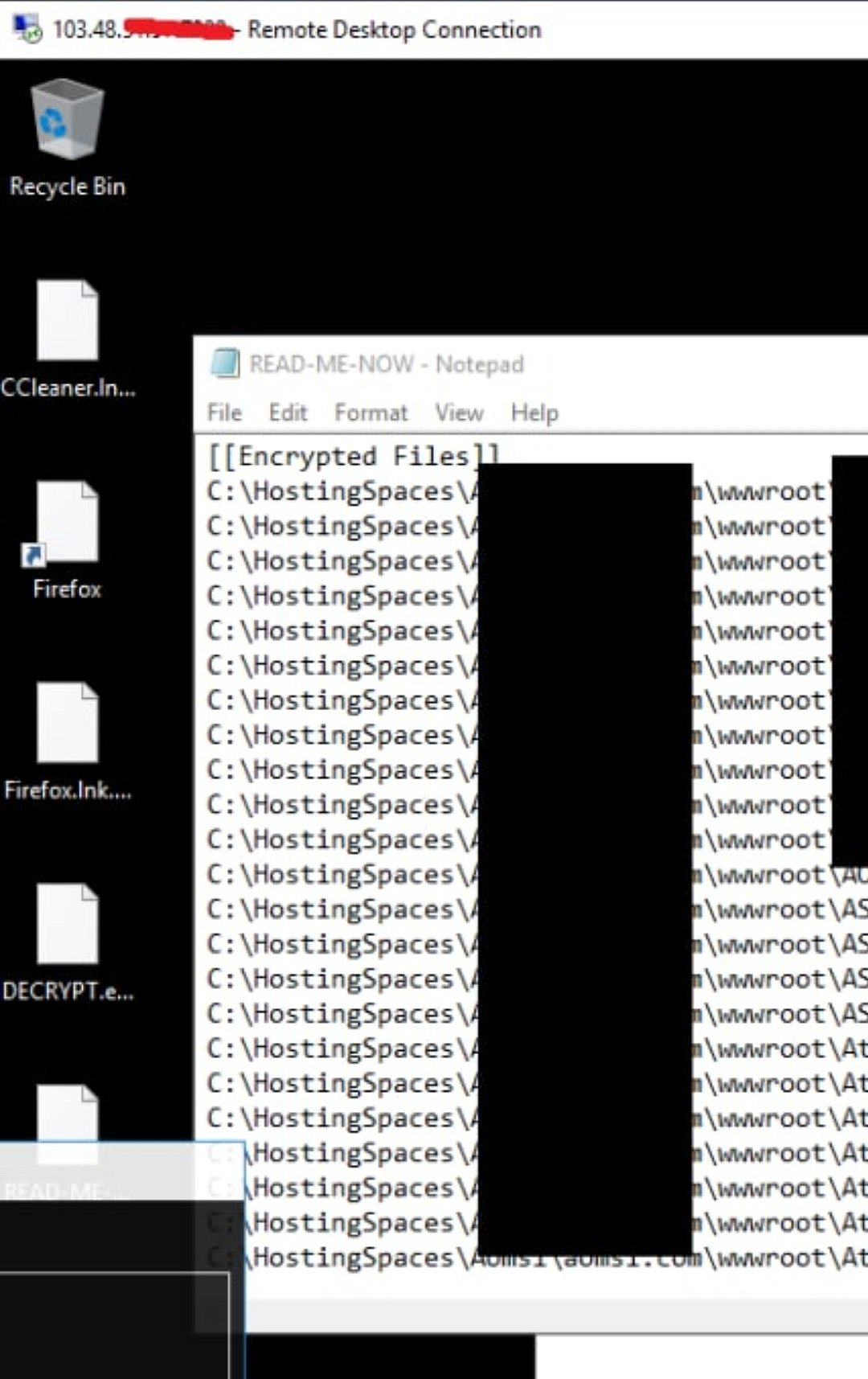
On Friday, DragonForce posted a screenshot of a hacked desktop screen, where all the desktop icons were changed to encrypted files that can not be opened without the encryption key. Certain data in the screenshot was blacked out, supposedly to hide the identity of the victim. The screenshot, which was posted on DragonForce’s dark web forum, was accompanied by a message saying that a ransom demand had been made.
“A ransomware is a very dangerous form of attack as it compromises all the data of the target as well as extorts money from them. However, there is no guarantee that even after the ransom is paid, the data will be returned. There have been numerous cases where the hackers have dumped the data on the internet even after receiving the ransom. Besides, a new technique is observed these days where bigger, more serious hacks are hidden under the guise of ransomware attacks,” a cyber crime officer said.
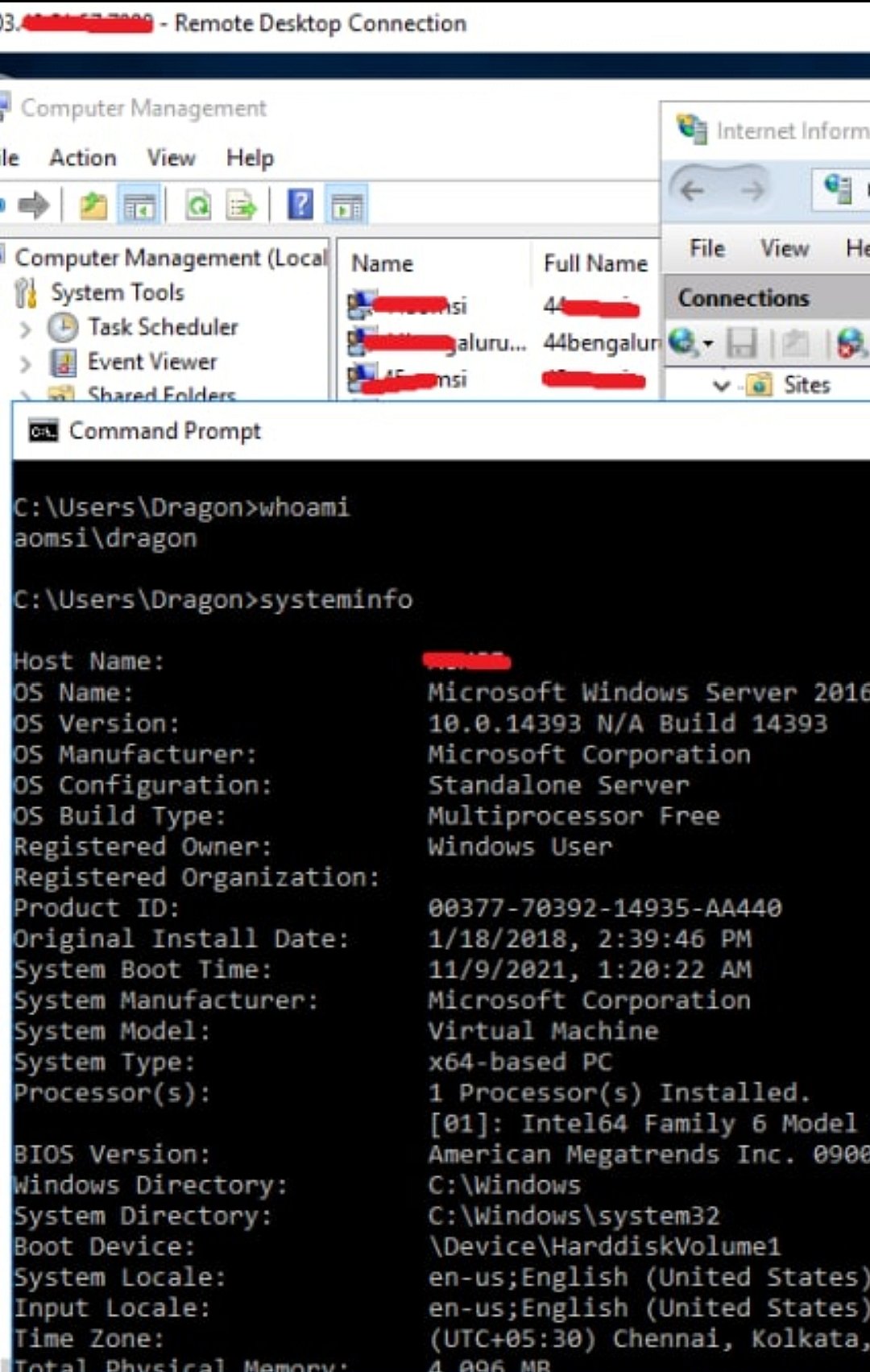
Since Thursday, DragonForce has also posted several other messages claiming to have hacked Indian Windows servers, which have been accompanied by screenshots and one Proof of Concept video, which shows the entire hacking process recorded while the hack is made. DragonForce claimed to have exploited existing vulnerabilities in Windows to gain Local Privilege Escalation (LPE) and Root Privileges.
As the name suggests, LPE grants undue rights and access to the hacker on a local network which, technically, should only be available to the user. Root Privileges signifies advanced unauthorised access which lets the hacker read and write any files on the system, perform operations as any user, change the system configuration, install and remove software, and upgrade the operating system, essentially granting the hacker complete control over the hacked system.