Apart from using a strong password, it is also advisable to use the two-factor authentication (2FA) security feature as an added layer of security to protect the email account in case the password is stolen. However, hackers are also working hard to find ways to hack into the email account by bypassing the 2FA protection. Researchers have found that a group of hackers from North Korea called "SharpTongue" is using the SHARPEXT malware to bypass 2FA and hack Gmail and AOL accounts.
What is the SHARPEXT malware attack?
According to the US-based cyber security firm, Volexity, SHARPEXT is a malicious browser extension, which gets installed on the browser without the end-users noticing it. The extension operates in such a way that its activity does not get logged in the "account activity." It bypasses the 2FA protection to read and download email and attachments from Gmail and AOL accounts.
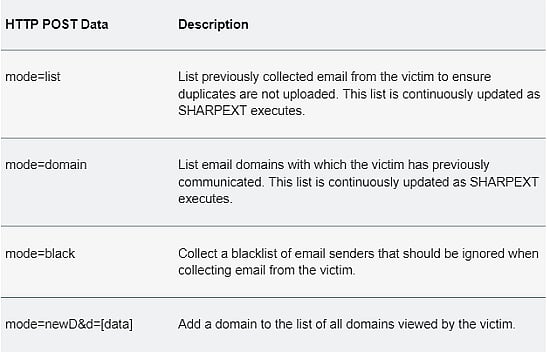
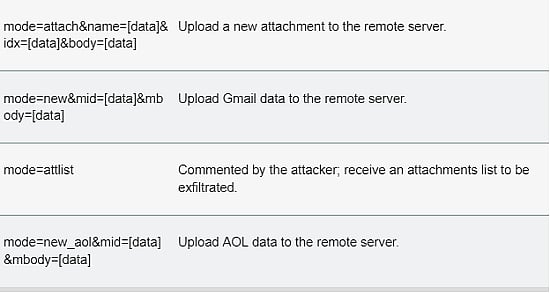
However, the SHARPEXT extension can be deployed only after the manual exfiltration of certain files from the target computer, such as a copy of the resource.pak file from the browser, users' S-ID value, and original Preferences and Secure Preferences. Once the preferences files are modified, the SHARPTEXT extension runs a PowerShell script to enable DevTools, which makes it possible to run customised code and settings. According to the cyber security firm, the extension can perform the following malicious requests:
How does it work?
The SHARPEXT malware attack works on Chromium engine-based browsers such as Google Chrome, Microsoft Edge, and Whale, a South Korean web browser. Researchers have found that the attack targets only Windows users. However, there is a possibility that the hackers may modify the attack to infect browsers running macOS or Linux in the future.
Who is at risk?
Volexity has said in its blog that SharpTongue mainly targets individuals from the US, Europe, and South Korea who work on topics related to nuclear issues, weapons, systems, or any other matters that North Korea considers important for its national security. As mentioned above, the malware mainly works on Windows devices.
How to stay protected from a SHARPEXT attack?
Volexity claims that SharpTongue has been using SHARPEXT on its targets for well over a year. It has been found that a dedicated folder is created for the infected users in each case. The folder contains all the required files for the extension.
Volexity recommends following these steps to detect and investigate SHARPEXT-like attacks.
1. Activating and analysing PowerShell ScriptBlock logging could be useful for identifying and finding a fix for a malicious attack.
2. Periodically review the installed extensions to check whether there are extensions that are not available on the Chrome Web Store or have been installed from an unreliable source.